Courses > Cybersecurity > Principles of Cybersecurity for Employees
It covers key topics such as cybersecurity terminology, security controls, identity and access management, cryptography, and incident response. The course aims to equip participants with the knowledge to understand and communicate about cybersecurity effectively, implement security controls, manage access to information securely, understand the basics of cryptography, and respond to cybersecurity incidents efficiently. By the end of the course, attendees will be prepared to both apply their knowledge in practical situations and pursue advanced studies in cybersecurity, fostering an environment of continuous learning and adaptation in the face of evolving digital threats.
This course will assist an attendee to prepare for the Certified in Cybersecurity Certification (CC) Exam from ISC2, the world’s largest network of certified cybersecurity professionals entity that helps them continue their professional development and earn new achievements and qualifications throughout their career. The topics on the CC exam included in this 2 hours with100 MCQ exam:
• Security Principles
• Incident Response, Business Continuity (BC) and Disaster Recovery (DR) Concepts
• Access Controls Concepts
• Network Security
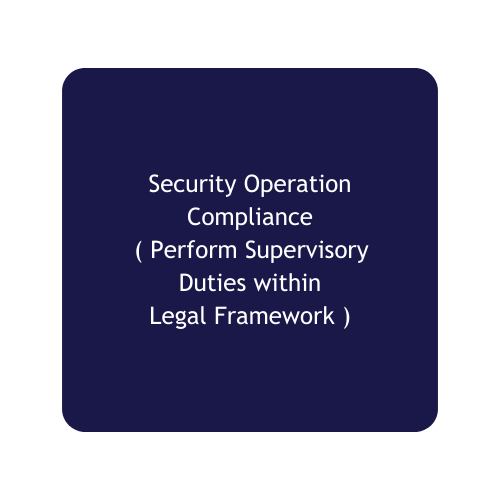
• Security Operations
In today’s digital landscape, both personal vigilance and organizational strategies are paramount in combating cyber threats. This comprehensive two-day course provides a deep dive into the fundamentals of cybersecurity and data privacy. Every employee, from entry-level to executive, plays a pivotal role in safeguarding their organization. Through this training, you will be prepared to actively contribute to your organization’s cyber defence strategy, enhancing both your personal security acumen and the collective resilience of your workplace.
You Will Learn
• Why is the need of cybersecurity and data privacy?
• What are the basic concepts and terms of security?
• What do I need to know about security risk and the basic controls?
• Why do we need security principles and what are they?
• What are the technical components of security?
• How to ensure secrecy of data and messages?
• How do we assert who requires access to secure data?
• What to do when a security breach occurs?
These Two-days cybersecurity fundamentals course is designed to give participants a foundational understanding of cybersecurity concepts and principles. Cybersecurity is a critical area of concern for individuals, businesses, and organizations alike, as cyber-attacks and data breaches can result in significant financial, reputational, and legal consequences. Each individual employee of any organization has his/her contribution of “See something, do something” to strengthen the Cybersecurity posture of the organization. Since, Security is every one’s responsibility.
Who Should Attend?
• Broad Audience: Any employee within any organization, regardless of role.
• Information Handlers: Individuals who access any organizational data or digital assets.
• Security-Conscious: Those concerned about cyber threats and organizational risks.
• Future-Oriented: Employees aiming to enhance their cyber risk management skills.
After completing this course, YOU/Employee will be able to:
• Appreciate the purpose of Information Security in the organization
• Contribute effectively to the objectives of Information Security in the organization
• Support the Objectives of Information Security in the organization
• Capable of instilling, practicing, and enhancing the Security Hygiene
• Appreciate the Cybersecurity Agency’s Cyber-Essential and Cyber-Trustmark standards
• Qualify to appear in the ISO/IEC 27001 Information Security Foundation training
• Qualify to appear in the ISO/IEC 27032 Cybersecurity Foundation training
• Apply the knowledge to prepare for entry-level Professional Certification, CC
Course Outline
• Topic 1: Cybersecurity and Privacy Introduction
– Introduction to Security: Information & Cyber.
– Purpose of Cyber Security and Data Privacy.
– Why is Cyber Security critical?
– How does Cyber Security and Data Privacy differ.
– History of Cyber security and its evolution.
– The Statistics and Status of Cyber Attacks.
• Topic 2: Concepts Terminology
– The Security TRIAD and DAD.
– The key concepts of Security.
– The fundamentals of Security.
– Layered Security principle.
– From Assets to Attacks.
• Topic 3: Security Risk, Policy, and Controls
– Cyber Security Policy, Procedures, Standards, and Guides.
– Cyber Threats. Vulnerabilities, and Risk
– Cyber Audit and Compliance.
– Control Safeguards and Countermeasures.
• Topic 4: Security Principles & Primaries
– The 5 Cyber Security principles: Governance, Protect, Detect, Response, and Recover.
– The 7 Privacy principles: General, Notice and Choice, Disclosure, Security, Retention, Data Integrity, Access Principle.
– The Key Threats, Vulnerabilities, Attacks and Controls
* Threats: Nation States, Terrorists, Criminals, Hackers, Malicious Insiders.
* Vulnerabilities: Zero Day, Poor input validations and Data Sanitisation, Unpatched Software, Unauthorized Access, Misconfiguration, Credential Theft, Vulnerable APIs.
* Attacks: Malware, Denial-of-Service (DoS) Attacks, Phishing , Spoofing, Code Injection, Insider, Identity-Based, IoT-Based, Supply Chain, DNS-based.
* Controls: Patching, MFA, Zero-Trust, restrict administrative privileges, application control, restrict untrusted application, systems hardening and regular backups.
• Topic 5: Security Elements
– 5 key security elements: Network, Information, Application, Operational, and End-user.
– Staying Secure While in the Office
– Staying Secure While out of the Office
• Topic 6: Cryptography
– Basics of Information secrecy and concealment
– Objective of Cryptography
– Common elements and methods: Cryptography, Cipher Algorithm, Key Lifecycle, Hash
– Practical Use of Cryptography
– Public Key Infrastructure (PKI) and its use
• Topic 7: Identity and Access Management
– IAAA Concepts
– Authentication: purpose and multi-Factors of Authentication.
– Authorization: Privilege, Permission and Rights.
– Access Controls: Types- Discretionary, Role based, and Attribute based.
• Topic 8: Incident Response
– Purpose and definition of Security Incidents
– Incident Stages
– Investigation and Forensics
– SOC: Tools and Techniques
• A concern for the protection of your organization against cyber threats.
• Your organization has been a victim or a potential a victim of any cyber-crime or scam.
• Basic proficiency in reading, writing, and speaking English.
Course Fee
• SGD$550.00 (Excluding GST) Prevailing GST rates apply
Course Duration
• Two (2) Days / Sixteen (16) Hours
10 – 11 July 2024 (Wed-Thurs)
05 – 06 July 2024 (Fri-Sat)
10 – 11 July 2024 (Wed-Thurs)
05 – 06 July 2024 (Fri-Sat)
05 – 06 August 2024 (Mon-Tue)
05 – 06 August 2024 (Mon-Tue)
05 – 06 September 2024 (Thurs-Fri)
05 – 06 September 2024 (Thurs-Fri)
01 – 02 October 2024 (Tue-Wed)
01 – 02 October 2024 (Tue-Wed)
26 – 27 December 2024 (Thurs-Fri)
26 – 27 December 2024 (Thurs-Fri)
2 days
[18 hrs]
$408.75
$146.25
$221.25
$76.30
The Course fee is to be paid by:
• Post-Secondary Education Account (Standing order form)
• SkillsFuture Credits (SFC)
• Paynow (e-payment)
• Cash





Don’t take our word for it, see what PROSPECT talents have to say.
TRAINEES


















































2 Alexandra Road, Delta House #03-02A Singapore 159919
O: +65 6820 8238
enquiries@prospectprotection.net
Operating Hours : 8:30 am – 6:00 pm
2024 © Copyright Prospect Protection. All Rights Reserved.